CYSEC software infrastructure security solutions are now available for Azure. ARCA Trusted OS can run in a confidential VM and boot following the attested launch protocol. This protocol delivers the promise of confidential computing by isolating a VM from all other processes running on Azure.
For organizations navigating the complexities of third-party virtualized environments, ensuring the integrity and authenticity of their virtual machines is paramount. That’s why CYSEC has been at the forefront of developing innovative software infrastructure solutions, including cutting-edge confidential computing technologies.
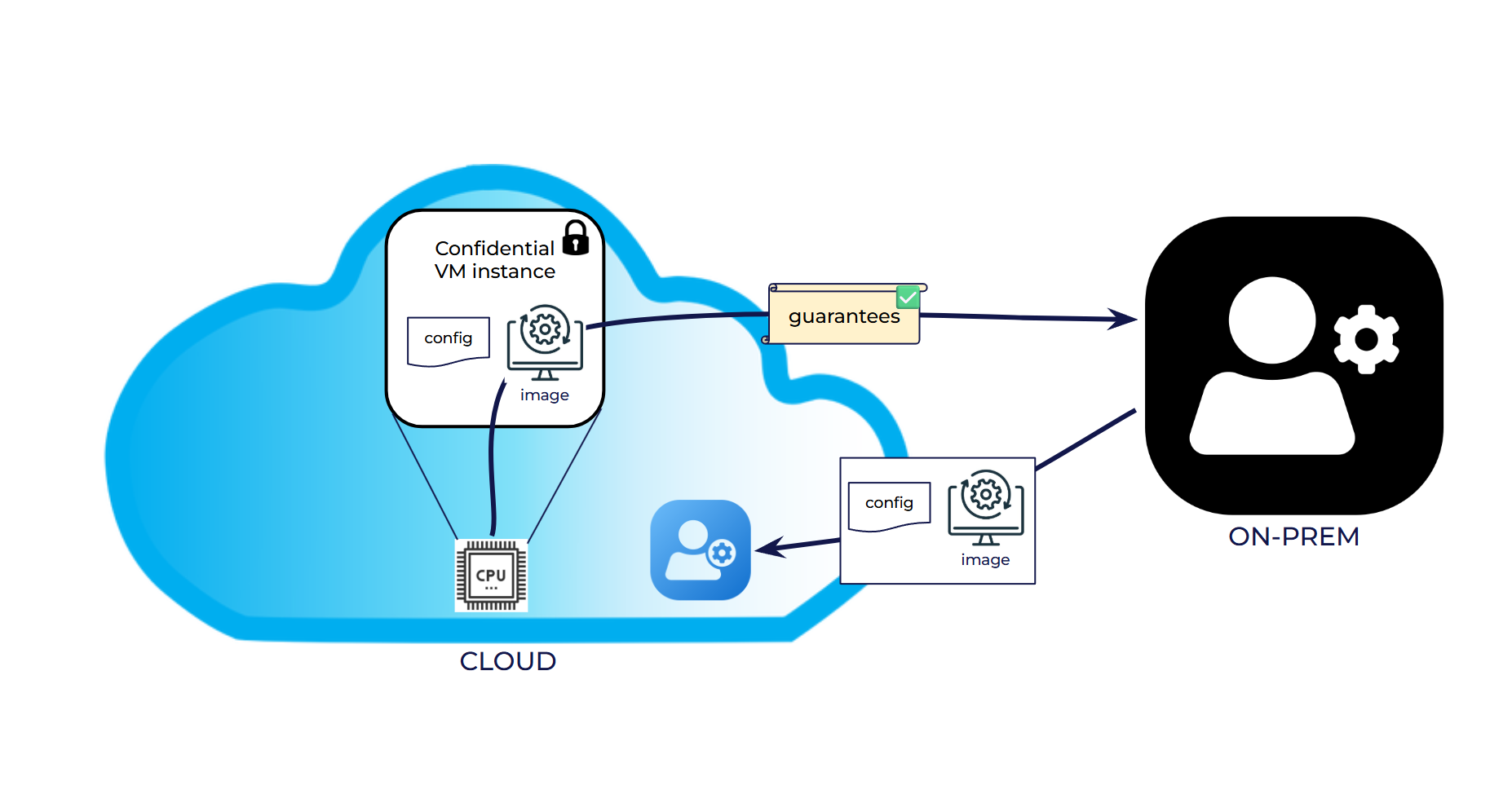
Our pioneering ‘attested launch protocol’ provides a robust mechanism for VM owners to gain verifiable trust in their cloud deployments. Imagine this: you provide your carefully crafted VM image and precise configuration to the cloud hypervisor. Upon launch, our protocol leverages the underlying CPU’s capabilities to generate cryptographic guarantees. These guarantees act as a digital fingerprint, allowing you, the VM owner, to definitively verify whether your exact image and configuration were used – untouched and untampered with – by the hypervisor. Based on this irrefutable evidence, you can confidently decide whether to trust the launched VM instance.
Figure 1: Simplified workflow of the CYSEC attested launch protocol
Building on this foundational technology, we’re pleased and excited to introduce our latest breakthrough: a complete software infrastructure solution that brings the power of attested launch to ARCA Trusted OS on Microsoft Azure.
Introducing ARCA Trusted OS on Azure: Boot with Unshakeable Confidence
ARCA Trusted OS, our hardened Linux-based microdistribution meticulously engineered for running containerized applications securely, now integrates seamlessly with Azure’s confidential computing capabilities
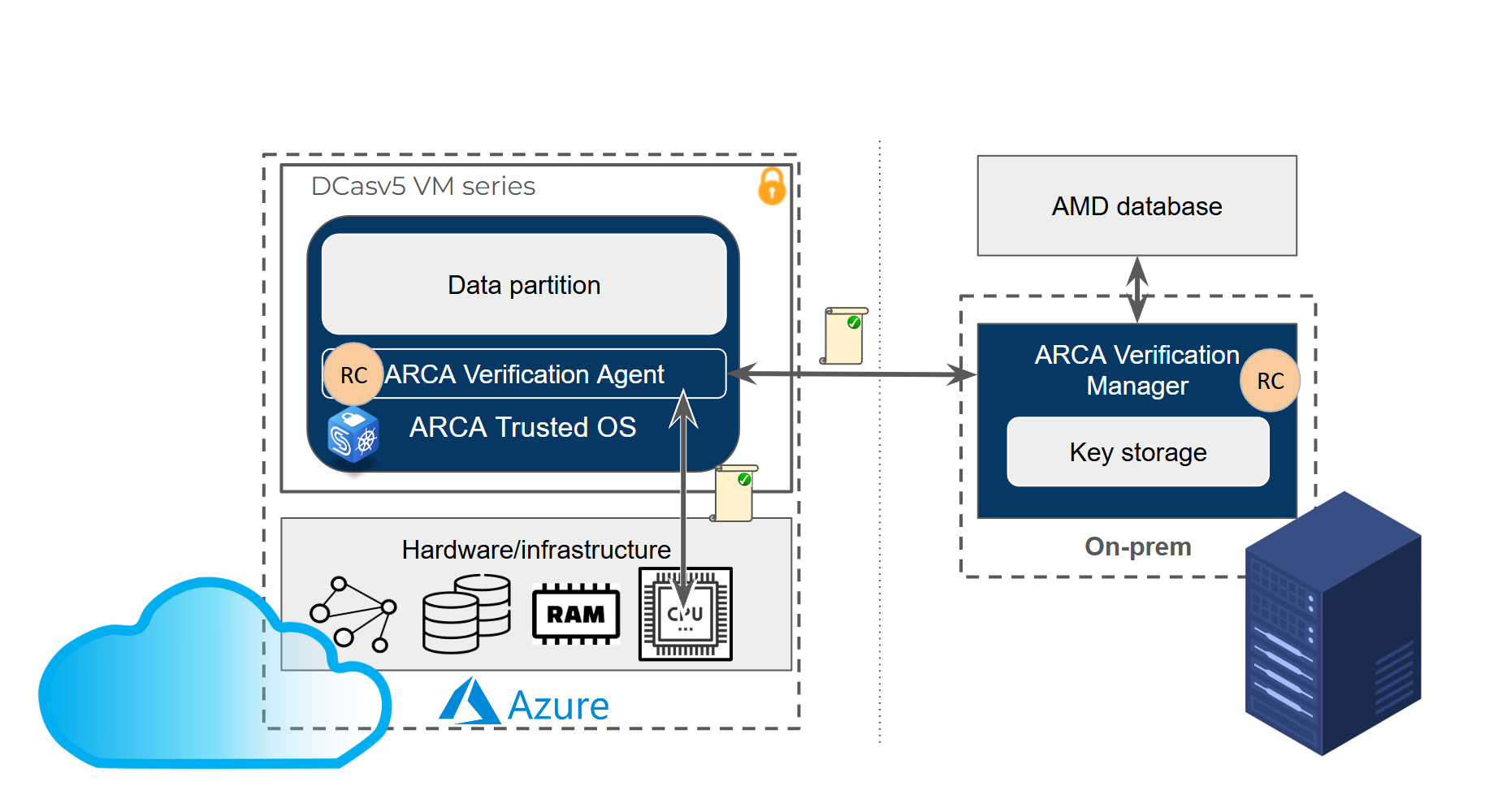
Figure 2: CYSEC architecture solution on Azure
Here’s how it works (see figure 2): When an ARCA Trusted OS instance boots within a confidential VM on Azure, an embedded intelligent agent initiates a crucial security step. It momentarily pauses the boot process to request a fresh, cryptographically signed attestation report directly from the underlying CPU. This report, a tamper-proof record of the boot environment, is then securely forwarded to the ARCA Verification Manager service.
This critical verification service resides entirely within your control, running securely on your premises. It meticulously analyzes the attestation report, validating its authenticity and ensuring the integrity of the boot process. Only upon successful verification does the ARCA Verification Manager grant permission for the VM agent to proceed with the boot sequence.
The result? An ARCA Trusted OS instance that completes its boot process only after its authenticity and integrity have been rigorously verified, backed by the unforgeable guarantees provided by the Azure hardware. This ensures that your sensitive workloads operate in a trusted environment, free from unauthorized modifications.
Your Path to Enhanced Cloud Sovereignty on Public CloudSecurity on Azure
Our comprehensive solution for Azure comprises a hardened and optimized ARCA Trusted OS image, along with all the necessary software components to easily install and operate your dedicated ARCA Verification Manager on your on-premise infrastructure. This gives you complete control over the verification process and keeps your sensitive verification keys within your trusted environment.
Ready to experience the next level of cloud security and deploy your containerized applications on Azure with unshakeable confidence?
Take the First Step Towards Full Cloud Sovereignty a More Secure Cloud: Contact our team today at info@cysec.com to explore how ARCA Trusted OS on Azure can fortify your cloud deployments.