The increasing prevalence of network-connected devices and the rise of the Internet of Things (IoT) have led to an urgent need for security mechanisms that can detect and protect against unauthorized access and data breaches.
Remote Attestation (RA) is a technique that has emerged as a promising solution for addressing these security concerns. RA provides a way to measure and verify the integrity of devices that are connected to a network, enabling organizations to identify and prevent security threats such as malware infections, data breaches, and unauthorized access.
CYSEC is currently tackling this topic within the the FLUIDOS project (HORIZON-CL4-2021-DATA-01), which aims to leverage the enormous, unused processing capacity at the edge, scattered across heterogeneous edge devices that struggle
to integrate with each other and to coherently form a seamless computing continuum.
This article provides an overview of RA, a short description of the process, and some of the types of measurements used. We then examine the different use cases and applications for RA, including how it can be used to detect and prevent security threats. We provide specific examples of how RA can be used in real-world scenarios, such as protecting industrial control systems from cyberattacks and ensuring the security of cloud-based applications.
RA is a security mechanism that allows a remote device to prove its identity and integrity to a remote party, this can help establish trust between two devices and ensure that they are communicating securely. (1)
In a typical RA scenario, the remote device, such as a computer or mobile device, generates a statement of its current state, or “attestation,” using a combination of hardware and software-based measurements. This attestation includes information about the device’s identity, firmware, software, and other system attributes. The attestation statement is then signed by a trusted authority, such as a certificate authority (CA), to ensure its authenticity.
The attestation statement can be sent to a remote party, such as a server or a network administrator, who can use it to verify the device’s identity and integrity. This can help detect and prevent unauthorized access, malware infections, or other security threats.
RA is commonly used in industries such as cloud computing, the Internet of Things (IoT), and critical network infrastructure to establish trust between devices and ensure secure communication.
Static and dynamic remote attestation are two different approaches to remote attestation, which differ in the types of measurements they use and when they are performed.
Static remote attestation is a form of RA that involves measuring the software and firmware’s integrity on a device at a fixed point in time, typically during boot-up or system initialization. The measurements taken during this process are
compared to a known set of values or a predefined policy, and an attestation statement is generated based on the comparison results. This statement can then be used to verify the device’s identity and integrity. Static RA is a one-time process
that provides a snapshot of the device’s state, and it cannot detect any changes that may occur after the measurements have been taken.
Dynamic remote attestation involves continuously monitoring the device’s state over time, using a combination of software and hardware-based measurements. These measurements are taken at various points during the device’s operation, and any deviations from a predefined policy or expected behavior are detected and reported. Dynamic RA provides a more real-time view of the device’s state and can detect any changes that may occur during its operation.
In RA procedures, one entity (Attester) produces information about itself (Evidence) to enable a remote entity (Relying Party) to decide whether or not to consider the Attester a trustworthy entity. RA procedures are facilitated by an additional entity (Verifier), which evaluates the Evidence through policies and creates the Attestation Results to support Relying Parties in their decision process.
Figure 1 shows an overview of the generic RA process, independent of protocol or use case (2).
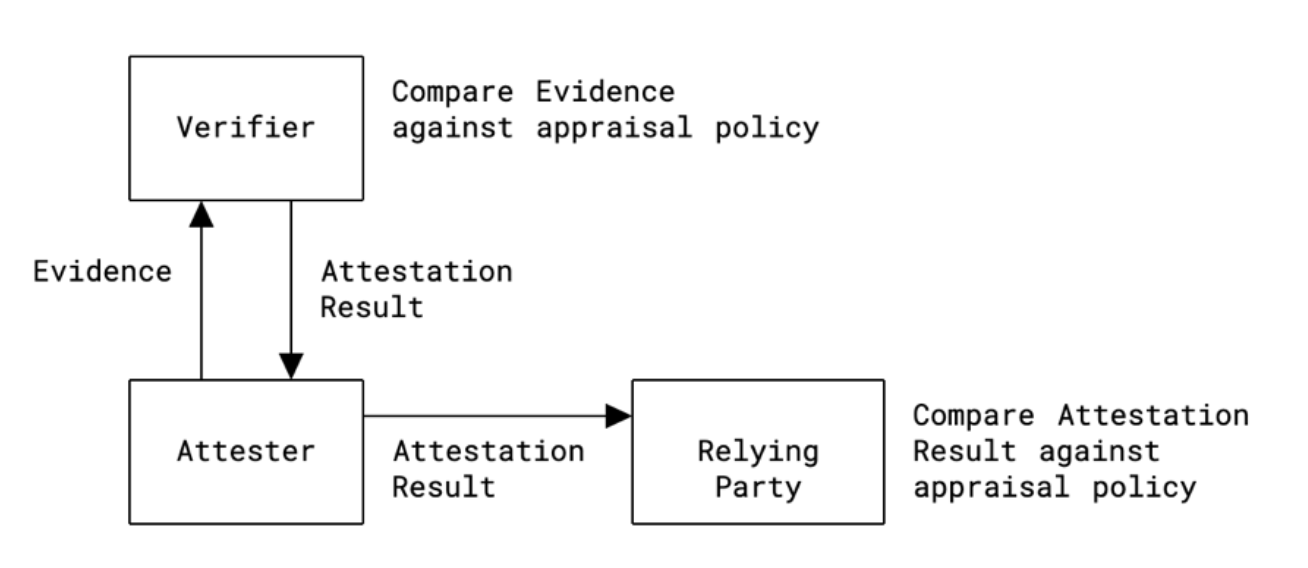
In this model, the Attester conveys Evidence to a Verifier, which compares the Evidence against its Appraisal Policy, if there are no processing errors, the Verifier then gives back an Attestation Result. If the Attestation Result was a successful one, the Attester can then present the Attestation Result to a Relying Party, which then compares the Attestation Result against its own Appraisal Policy.
There are different types of measurements used in RA, including software-based, hardware-based, and hybrid measurements. The measurements used in RA depend on the specific attestation mechanism used, but in general, they can include the following types of measurements:
RA has a variety of use cases and applications in different domains, such as cloud computing, Internet of Things (IoT), supply chain security, and network security. Following are some examples of use cases and applications for RA, including examples of real world scenarios.
4.1 Cloud Computing: RA can be used to establish trust between cloud service providers and their clients, by verifying the identity and integrity of the cloud infrastructures, like virtual machines (VMs), and software applications running on it. RA can also help prevent unauthorized access to cloud resources and ensure compliance with security policies (3). One specific area where RA can significantly impact cloud security is in the context of confidential computing, which leverages Trusted Execution Environments (TEEs).
At a minimum, RA in cloud computing should provide a cryptographic proof that consists of:
Confidential Space by Google Cloud
In December 2022, Google announced the release of Confidential Space, a new solution that allows access control to sensitive data and secure collaboration. (4)
Confidential Space leverages TEEs to give data contributors control over how their data is used and who can access it. The system has three main components:
Below is an overview of the overall workflow.
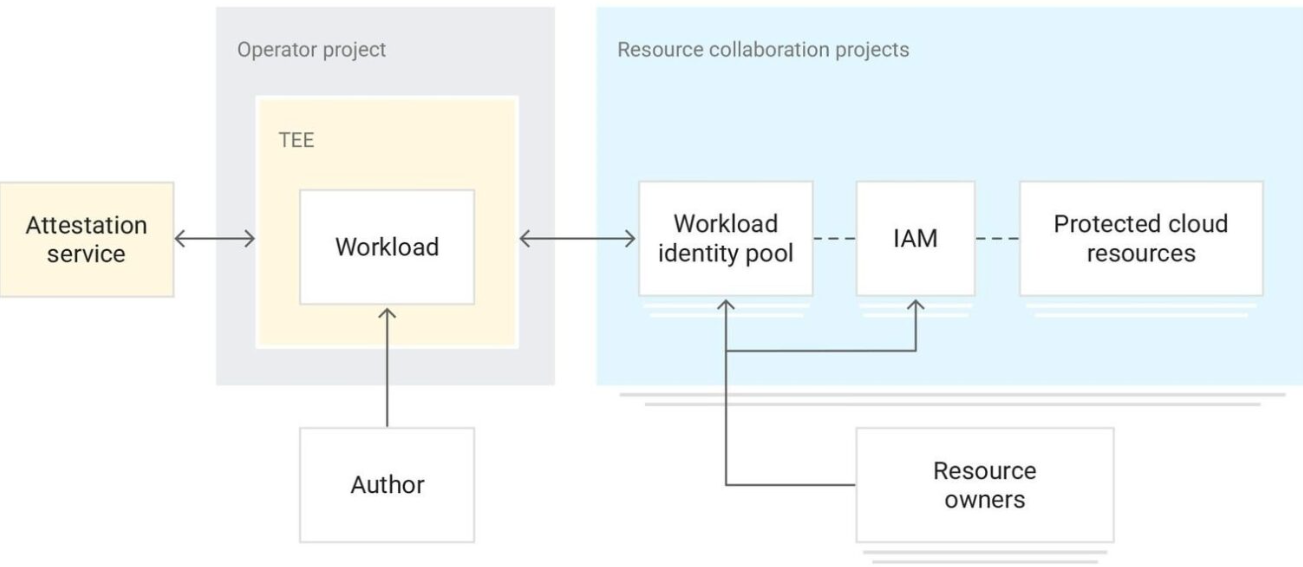
Real world scenario of RA in Cloud Computing
The web hosting company GoDaddy suffered its third data breach in three years that resulted in the compromise of the login credentials of over 28,000 customers (May 2020), theft of the source code for Managed WordPress servers (November 2021), and malware installation on GoDaddy’s cPanel hosting servers (December 2022). (5)
One way that RA could have helped prevent the breaches is by providing an additional layer of security to verify the identity of the user and the integrity of the device accessing the cloud application. By using RA to verify that the user’s device is running trusted software and has not been compromised by malware or other security threats, cloud service providers can reduce the risk of credential stuffing attacks and other types of cyberattacks that rely on compromised endpoints.
In addition, remote attestation can help ensure that cloud applications are running in a secure and trusted environment, protecting against threats such as unauthorized access, data exploitation, and malware infections.
4.2 Internet of Things (IoT): One fundamental IoT security component is making sure devices and services have trusted identities that can interact within secure ecosystems. RA can be used to establish trust between IoT devices and their service providers, by verifying the identity and integrity of the devices and software running on them. RA can also help detect the presence of malware in a remote untrusted IoT device, which typically has to stop its regular operations to perform the computations. This process will however consume the battery life of the device. To solve this problem, Remote Attestation as a Service (RAaS) comes into play. RAaS aims at checking the integrity of an untrusted device by performing the attestation computation on the cloud, allowing even a low-end IoT device to securely offload the attestation process to the cloud (6).
Real world scenario of RA in IoT
In 2017, the cybersecurity firm Armis discovered a set of vulnerabilities in Bluetooth-enabled IoT devices that enabled attackers to take over the devices remotely. The vulnerabilities, collectively known as “BlueBorne,” affected over 5 billion devices worldwide, including smartphones, laptops, and smart home devices (7). To protect against BlueBorne and similar attacks, Armis developed a remote attestation system called “Armis Trust,” which uses machine learning algorithms to detect anomalous behavior in IoT devices and trigger remediation actions in real-time.
The Armis Trust system works by monitoring the behavior of IoT devices and generating an attestation report that summarizes the device’s behavior and security posture. The report is then compared to a set of policies that define acceptable behavior for the device. If the device is found to be in compliance with the policies, it is allowed to continue operating. If the device is found to be non-compliant, the system can quarantine the device or trigger remediation actions, such as firmware updates or security patches. By using RA to monitor the behavior of IoT devices in real-time, the Armis Trust system can detect and prevent attacks that exploit vulnerabilities in the devices’ software and firmware.
4.3 Industrial Control Systems (ICS) Security: RA can be used to secure ICS by ensuring that the software running on ICS devices has not been tampered with and is up to date. For example, in a power plant, RA can be used to verify that the control systems are running the latest firmware and that they have not been compromised by malware. This can help prevent cyberattacks on ICS and ensure the safe and reliable operation of critical infrastructure.
Real World Scenario of RA in ICS Security
In 2021, the Colonial Pipeline, which supplies fuel to much of the eastern United States, was hit by a ransomware attack that caused the company to shut down its operations. The attack was successful because the attackers were able to gain access to the company’s IT systems, which were connected to the industrial control systems that manage the pipeline’s operations (8).
RA can be used to prevent attacks like the one that targeted the Colonial Pipeline by verifying the integrity of the control systems in industrial environments. By measuring the state of the control systems and comparing these measurements to known trusted measurements, RA can detect any unauthorized modifications to the systems that could indicate an attack. This can help prevent the kind of damage that could result from a successful cyberattack on industrial control systems.
RA can be an important tool for protecting critical infrastructure from cyberattacks, ensuring the safe and reliable operation of industrial control systems in the face of evolving threats.
4.4 Confidential Computing (CC): There isn’t confidential computing without attestation. For example, if we want to deploy applications using CC on a public cloud, we need to take advantage of an attestation measurement, provided by TEE capabilities. But doing a cryptographic check of an attestation measurement is tricky, that’s why RA is needed, a service running on a different machine which can be trusted to validate the attestation and stop execution if it fails (9).
Real world scenario of RA in CC
One use case for confidential computing is in financial services, where sensitive customer data such as financial transactions and personal information must be kept secure. RA can be used to verify the integrity of the hardware and software running in a confidential computing environment, ensuring that the sensitive data is protected from unauthorized access and tampering.
For example, Microsoft Azure offers a confidential computing platform called Azure Confidential Computing, which uses Intel SGX technology to protect sensitive workloads. Here, RA is used to verify the integrity of the hardware and software running on the SGX-enabled processors, ensuring that the confidential data is protected from cyberattacks. (10)
By implementing RA, financial services organizations can provide a higher level of security for their customers’ sensitive data, reducing the risk of data breaches and cyberattacks.
4.5 Network Security: RA can be used to establish trust between network endpoints, by verifying the identity and integrity of the endpoints and the software running on them. RA can also help prevent unauthorized access and malicious attacks on network resources and ensure compliance with security policies. Network operators want trustworthy reports that include identity and version information about the hardware and software on the machines attached to their network. Typically, a solution starts with a specific component (referred to as a “root of trust”) that often provides a trustworthy device identity and performs a series of operations that enables trustworthiness appraisals for other components. Such components perform operations that help determine the trustworthiness of yet other components by collecting, protecting, or signing measurements (2).
Real world scenario of RA in Network Security
An example of a cyberattack in network security that could have potentially been prevented with RA is the SolarWinds supply chain attack that was discovered in December 2020 (11). The attack involved a sophisticated compromise of the SolarWinds Orion software, which is widely used for network management by thousands of enterprises and government agencies worldwide. The attackers were able to insert malicious code into the software during its development process, which then spread to numerous organizations that used the software.
RA could have potentially helped detect the malicious code in the SolarWinds software by measuring the integrity of the software during its development and deployment. By verifying the integrity of the software at various stages, RA could have alerted organizations to the presence of the malicious code and prevented its spread to other parts of the network. While RA is not a foolproof solution and cannot prevent all types of cyberattacks, it can be a valuable tool for detecting and mitigating threats in network security.
In conclusion, remote attestation is a powerful security technology that enables the verification of the identity and integrity of remote devices and systems. By providing a way to measure and verify the trustworthiness of endpoints and cloud infrastructure, RA can help organizations detect and prevent a wide range of cyberattacks, including unauthorized access, malware infections, and data breaches.
As the threat landscape continues to evolve, RA will become an increasingly important tool for ensuring the security and trustworthiness of remote devices and cloud infrastructure. By adopting RA and other advanced security technologies, organizations can help mitigate the risks of cyberattacks and protect their sensitive data and assets.