Today’s business dynamics put IT organizations under significant pressure to deliver agility, scalability, and resilience.
The adoption of public cloud platforms has become a proven strategy for companies seeking to expand their infrastructure and quickly adapt to fluctuating demand. However, for many organizations, concerns remain about the exposure of sensitive corporate data and the strict regulatory landscape that governs data protection and operational resilience.
Regulations such as the EU’s DORA Act, AI Act, and GDPR make it challenging for enterprises to move critical workloads to external environments without compromising compliance and security.
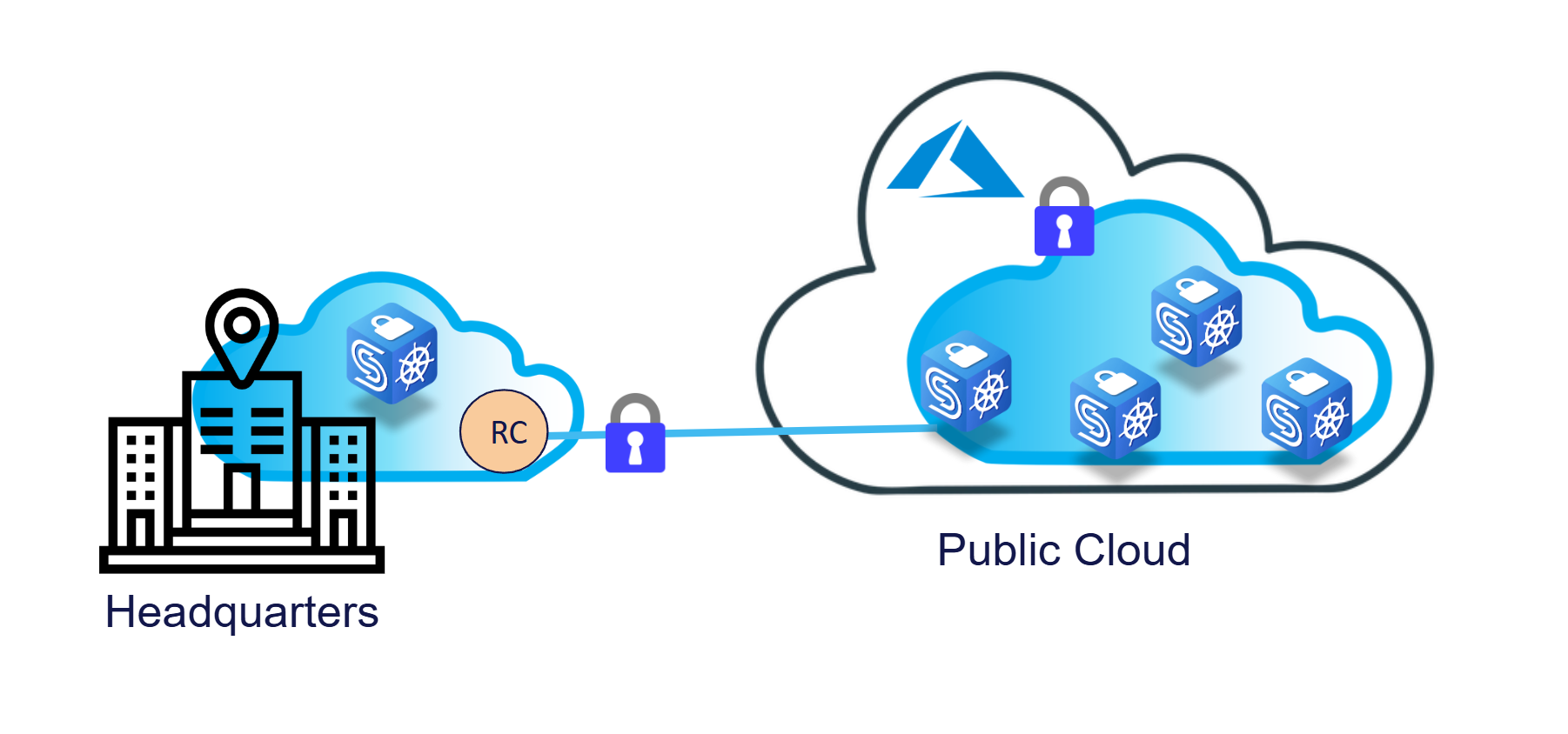
CYSEC addresses this challenge by offering a secure foundation for extending traditional on-premises infrastructure into the public cloud. By combining confidential computing, system hardening, and remote attestation, CYSEC creates trusted execution environments, also known as enclaves, that isolate sensitive applications and data (encryption in all states) wherever they are deployed. This includes public or private clouds, edge environments, or partner infrastructures.
In public cloud scenarios such as Microsoft Azure, CYSEC’s solution allows enterprises to leverage the scalability and elasticity of public cloud resources while maintaining complete privacy and control over their data. Sensitive assets are protected from any external or internal exposure, ensuring that corporate data remains secure even in shared environments. Companies can confidently deploy critical workloads to the cloud without surrendering control of encryption keys or trust mechanisms to public cloud service providers.
This approach is particularly valuable for sectors such as banking and financial services (BFSI), life insurance, retail, manufacturing, governmental organizations, and supply chain or logistics.
These industries handle highly regulated or confidential data and often require strong guarantees of data integrity and confidentiality when interacting with their partner and customer ecosystems.
With CYSEC, they can create a secure, trusted layer on top of public cloud infrastructure that mirrors the protection standards of their on-prem environments.
The key benefits for companies adopting this hybrid security model include the ability to scale flexibly with public cloud capacity while retaining on-prem-like control and visibility.
Organizations can bring their own encryption keys and manage them internally, maintaining full ownership of their data security. The solution ensures no dependency on cloud service providers within the chain of trust. This architecture enables business continuity, reduces operational risk, and minimizes the effort required to manage hybrid environments.
By replicating on-premises security models in the public cloud, companies gain the freedom to innovate faster, reach customers more efficiently, and collaborate with partners securely. The result is a hybrid IT ecosystem that delivers both agility and compliance—two qualities often seen as contradictory in traditional cloud adoption strategies.
With CYSEC, enterprises can finally expand their digital footprint beyond their physical data centers into the cloud securely and confidently, ensuring that their growth never comes at the expense of data privacy or operational control.