Are confidential VMs sufficient to isolate your containers from any cloud administrators?
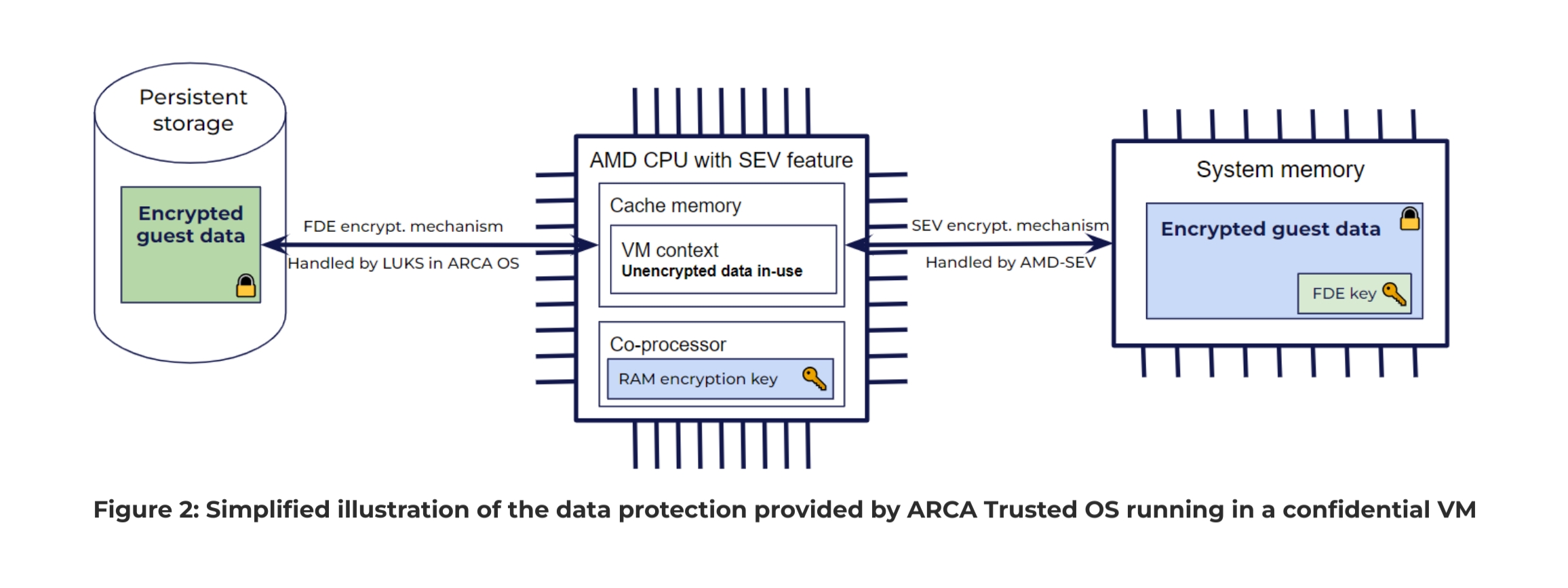
The aim of confidential VMs is to isolate a VM from its hosting environment, i.e. the host OS and the hypervisor. In a previous blog article, we explained how CYSEC can help you to migrate your sensitive data to public clouds. In this previous article, we described two important aspects that need to be considered when you try to isolate your data and workloads from any CSP admins. Firstly, CSPs provide many managed services that are extremely valuable from an operational point of view but might give access to the admins of these services to your data. This is particularly true in the context of container orchestration with Kubernetes. The admins of Kubernetes control plan have the capacity to access any containers running in the Kubernetes cluster even if the nodes are executed in confidential VMs. Secondly, confidential VMs provide protection of your data while in-use, i.e. stored in volatile memories. This protection isolates your data from host OS and hypervisor administrators when your data is stored in RAM. However it doesn’t help for the security of your data located in the image of your instances. The present article will describe the complementary security mechanisms that CYSEC provides you to address the second aspects when you want to isolate from any CSP admins.
What security measures CYSEC provides on the top of Confidential Computing to help you to isolate your containers and their data from public cloud providers?
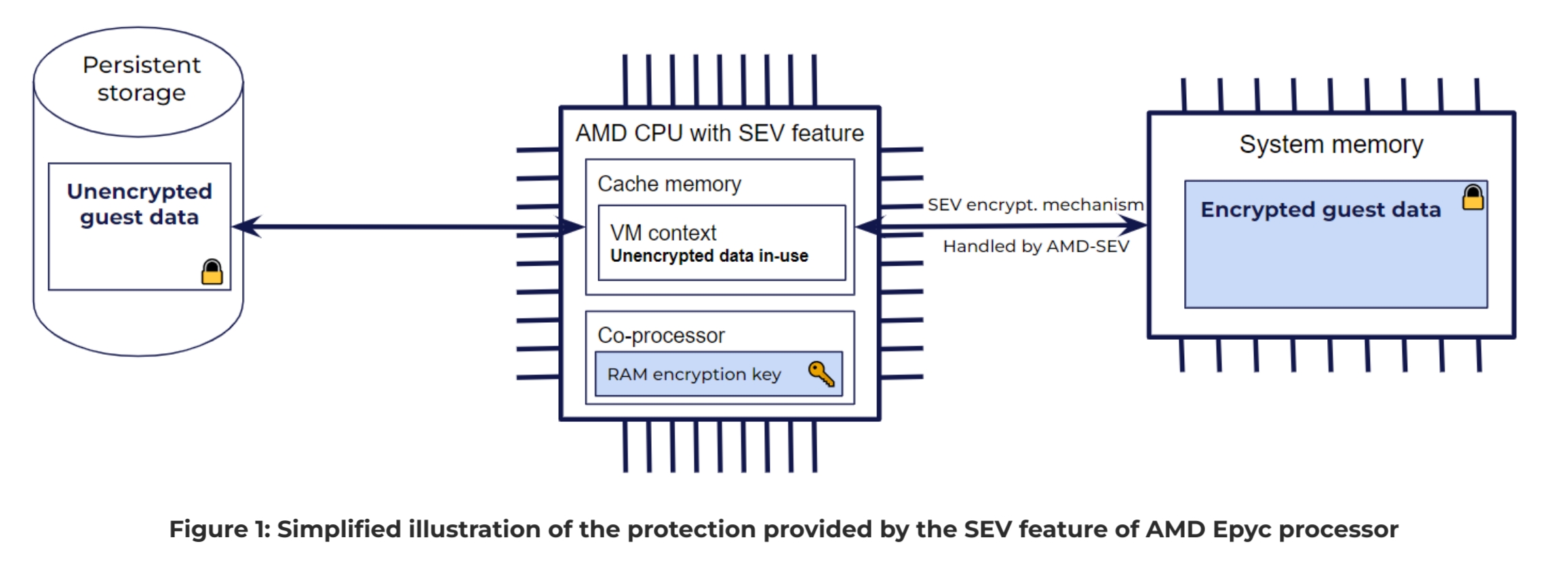
Confidential Computing is the protection of data in use by performing computation in a hardware-based Trusted Execution Environment (TEE). This TEE can be used to isolate certain software packages such as a VM, a process, a container or a library. This hardware-based TEE is offered by processor providers. Each processor provider has its own technology of TEE. CYSEC presently supports the Secure Encrypted Virtualization (SEV) feature from AMD Epyc CPUs. AMD-SEV feature generates a hardware-based TEE to isolate a VM. This feature is based on a secure co-processor (embedded in AMD CPUs) in charge of keys and encryption before storing data in the RAM. A simplified view of the isolation mechanism provided by AMD-SEV is illustrated in Figure 1. This illustration shows that the live data of a guest is encrypted before being sent to the system memory (RAM). It also shows that the data stored in the cache memory of the CPU is unencrypted for being processed. One important security aspect that is not shown in Figure 1 is that the context of each VM executed on the same CPU is isolated from each other and from the host context in the cache memory.