Indeed, CYSEC continues its edge computing strategy expansion by qualifying two mini servers after having qualified several x86 servers for data centers and two small ARM computing boards.
CYSEC proposes a solution designed to secure and facilitate the operation of containerized applications on distributed architectures. This solution relies on a Linux-based micro distribution, called ARCA Trusted OS, optimized to run containers. ARCA Trusted OS provides both a trusted computing base (TCB) for container management tooling (such as k8s) and a by-default protection of the end-user data. ARCA trustworthiness and data protection mechanisms are anchored in hardware roots of trust. ARCA Trusted OS security hardware prerequisites impose a qualification of the hardware. However, a qualification is feasible as long as a UEFI firmware and a TPM (Trusted Platform Module) are present.
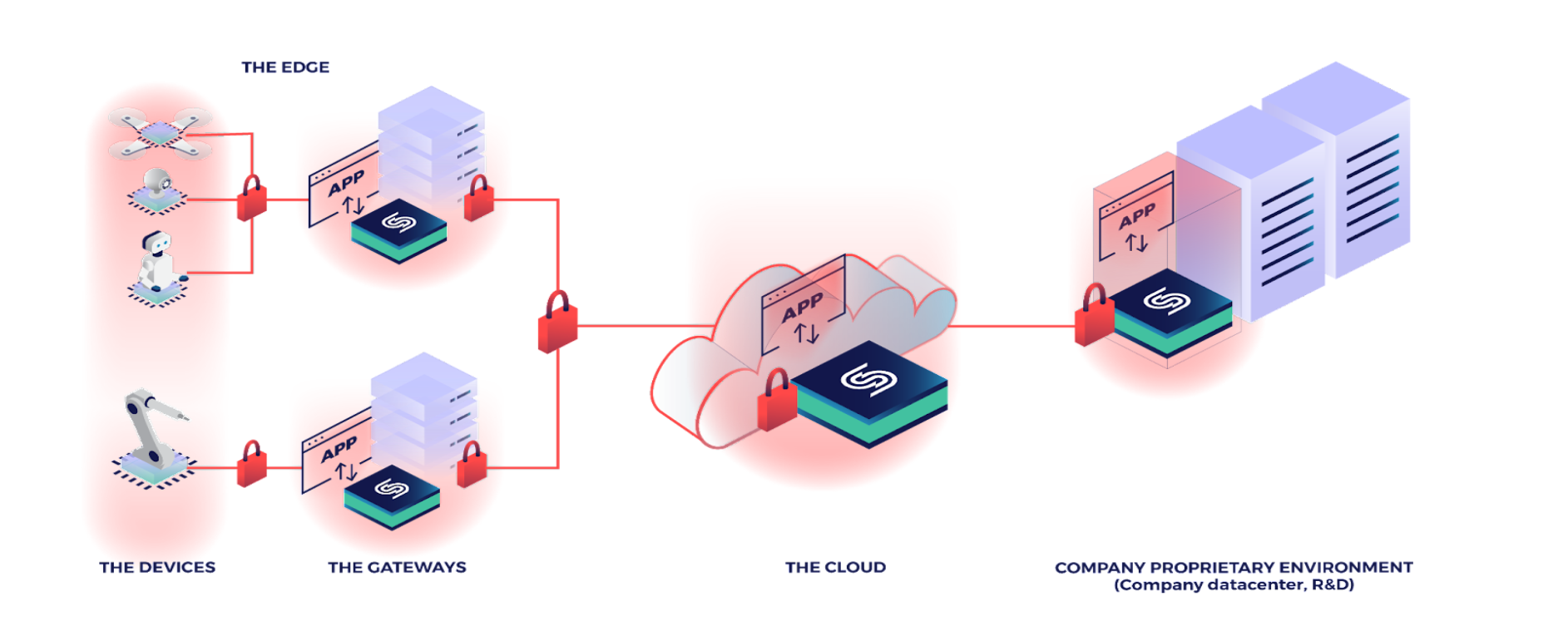
More and more applications deployed at the edge are pretty demanding in terms of resources. It is for example the case of applications exploiting AI/ML models. For such deployments, mini servers can be a good compromise between hardware cost and resources. This is the reason why CYSEC has qualified ARCA Trusted OS for several mini servers to allow its customers to protect their containers in such devices.
Presently, ARCA Trusted OS for x86 can be deployed on two mini servers:

ARCA Trusted OS for x86 comes with a full disk encryption (FDE) by-default that enforces the encryption of the data stored in the hard-disk of the miniserver. While the miniserver is switched off, the FDE key is stored in a physical TPM 2.0 or a fTPM (firmware TPM). This key is released from the TPM after a successful verification of the authenticity and integrity of ARCA Trusted OS at each boot. Under this condition, a copy of the FDE key is stored in the RAM for the on-the-flight encryption/decryption of the data while transferred between the hard-disk and the volatile memories.
This solution ensures that the data is always encrypted while in hard-disk. Such encryption solution is particularly important for edge servers that are deployed in public areas where their physical protection is limited, as for example in airports, hospitals, shops or autonomous vehicles. Indeed, the risk of theft of an edge server is pretty high in such public environments while the privacy of the data processed by these mini servers can be subject to strict regulations. Furthermore, the provider of the business logic processing the data (e.g. AI algorithm) might want to protect its intellectual property from this type of threat.
Moreover, for the most sensitive cases, the FDE mechanism can be associated with a mechanism of encryption of the data in the RAM to prevent an advanced attacker from getting access to the FDE key while it is in the RAM using the so-called cold boot attack or bootkits and rootkits. ARCA Trusted OS allows the activation of such RAM encryption such as the one proposed by AMD Ryzen and called Secure Memory Encryption (SME). This extended solution offers encryption of the data and code while they are in persistent and volatile memories.
If you want to try ARCA trusted OS or qualify another mini server, please send an email to info@cysec.com.