
Web
ARCA TRUSTED OS
A container-specific OS to provide a Trusted Execution Environment (TEE) for containers
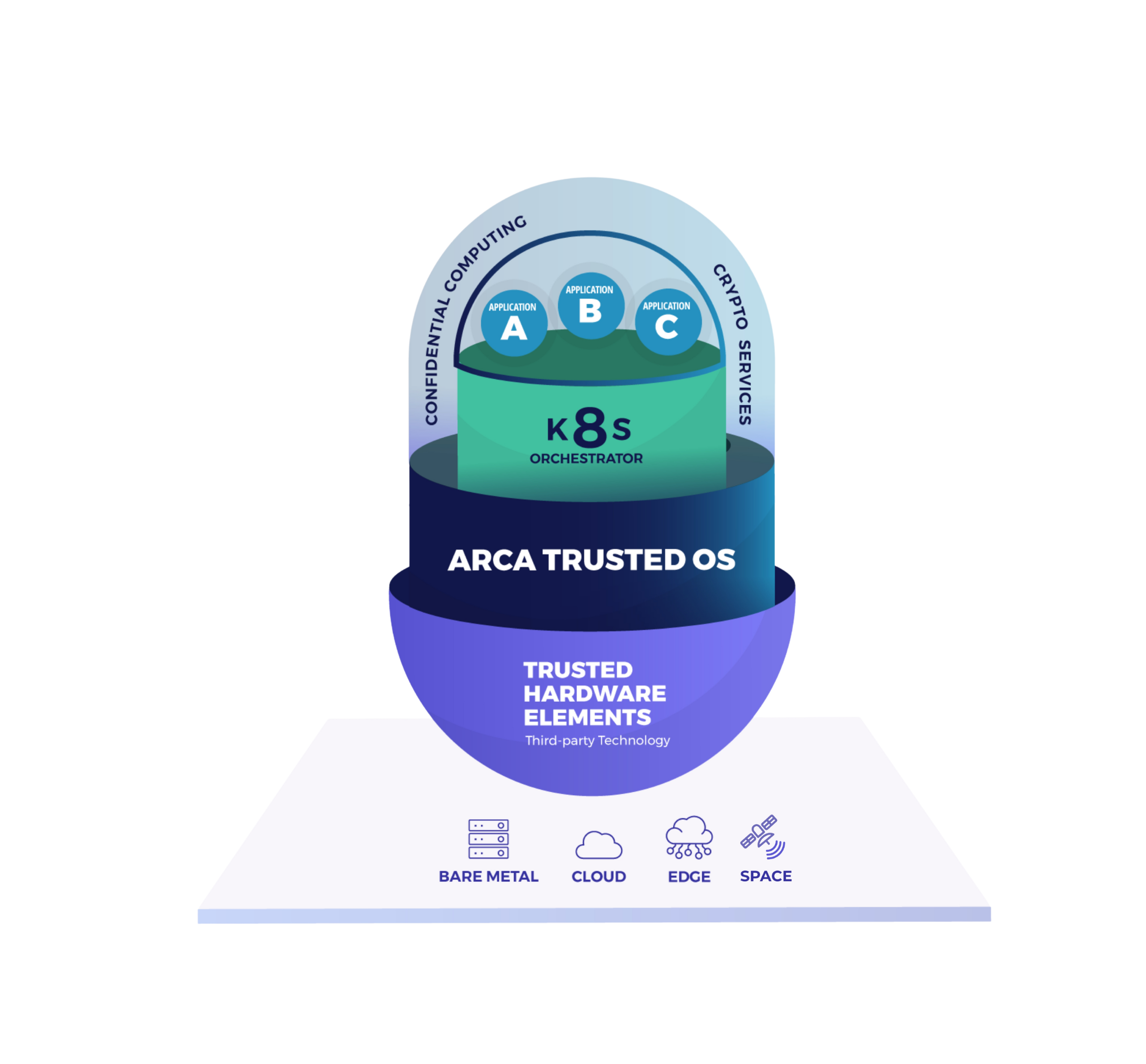

A container-specific OS to provide a Trusted Execution Environment (TEE) for containers

Arca Trusted OS is a hardened Linux-based operating system combined with a secure Kubernetes orchestrator to contain system intrusion and avoid data compromission in your containers on premise, on the cloud and, on the edge.
ARCA provides functions to protect keys, data & code and eases the adoption of Confidential Computing.


CONTEXT
Container Operating Systems are virtual environments where your container runs. Any vulnerability in the operating system could compromise the security of the containerised applications.
HOW WE HELP?
We reduce and mitigate the risk of system intrusion and data compromission in your container environments
THREATS OF SYSTEM INTRUSIONS AND DATA COMPROMISSION
Protects the OS from corrupted workloads.
Prevents from booting a corrupted or unauthorized OS.
Prevents from any modifications of the OS.
Prevents from updating to an unauthorized OS.
Container-specific OS
Hardware Root of trust
Chain of trust with extended secure boot
Container runtime protection
Immutable OS
Data at rest protection
Data in use protection
Data in transit protection
Full Disk encryption (by default)


PROTECTION
• Protect your data at rest, in transit, and in use on infrastructure you do not own and control.
• Isolate your data from cloud providers admins
SIMPLIFICATION
• Adoption of the confidential computing
• Hardening specific activities related to container management
COMPLIANCE
• NIST SP 800-190 recommendation on container security
• With strict data protection regulation

“CYSEC doesn’t just identify the security vulnerabilities in a fintech environment, it provides prioritized remediation advice, and then validates implementation. I recommend CYSEC LAB to any fintech player needing pentesting services.”

“We are very happy with the service provided by CYSEC LAB. We are impressed with the rapid comprehension of our needs and preliminary architecture design, appreciated their clear advice and high availability.”

“CYSEC was extremely flexible throughout our engagement, which enabled us to meet complex business objectives. They worked to our multi-milestone schedule, and respected our priority order for feature deployments. Further, they showed an impressive ability to adapt to our changing timeframe and evolving demands during the deployment. They were professional, responsive, and rapid.”

“We've been partnering with the CYSEC ARCA Trusted OS for over two years. Our customers are among the largest and most sophisticated financial services companies in the world and we've been able to consistently and successfully service them with ARCA. We would recommend the product to others.”
