Edge computing in IoT is developing rapidly, driven by next-generation connected devices and fast communication links. Gartner predicts that by 2025, 75% of enterprise-generated data will be created and processed at the edge. As value shifts toward decentralized computing, security gaps emerge in cloud-edge integration and edge devices become an entry point for attacks.
Project sponsor: DIGIFED (funding from the European Union’s Horizon 2020 research and innovation programme)
Start: November 1st, 2020
Duration: 9 months
Technology: ARCA Trusted OS / ARM TrustZone / TPM
Market: IoT
Expected outcome: Hardware-based cryptographic back-end for PKI and other IoT applications.
The goal of the project is to develop a lightweight distribution of ARCA Trusted OS which can run on a router. This router is available on the Edge to be used by other connected objects before the information is transmitted to the cloud.
A compelling application in an IoT topology is Public Key Infrastructure (PKI). A PKI is a set of techniques and tools to manage public-key cryptography. One of the main concerns of a PKI is how to protect private keys. The ultimate goal of an attacker on a PKI system is to get the hands on the so-called root Certificate Authority (CA) private key in order to be able to sign arbitrary requests and therefore impersonate any user of the system that was hardened in order to reduce the attack surface.
In this project we were interested in managing access and roles on a Network-Attached Storage (NAS) device (or other multi-tenant devices available at the Edge). Users can connect via Virtual Private Network (VPN) or HTTPS and perform a number of actions. The NAS is therefore running a hardware-based mini-CA of its own and distributes certificates to the users.
This mechanism enables access control and audit trail of interactions with the NAS. Usually because of cost efficiency, a typical NAS server does not have a notion of Secure Element (SE) for secure storage of sensitive keys. In the case of a typical PKI, technologies such as Hardware Security Module (HSM) are used to store and protect CA private keys. HSMs are proven secure but very expensive and not straightforward to use. Therefore, the goal of this project was to investigate the possibility of using a pluggable and cost-efficient cryptographic secure module to store sensitive key materials and perform cryptographic operations on behalf of mini-CA running on the NAS.
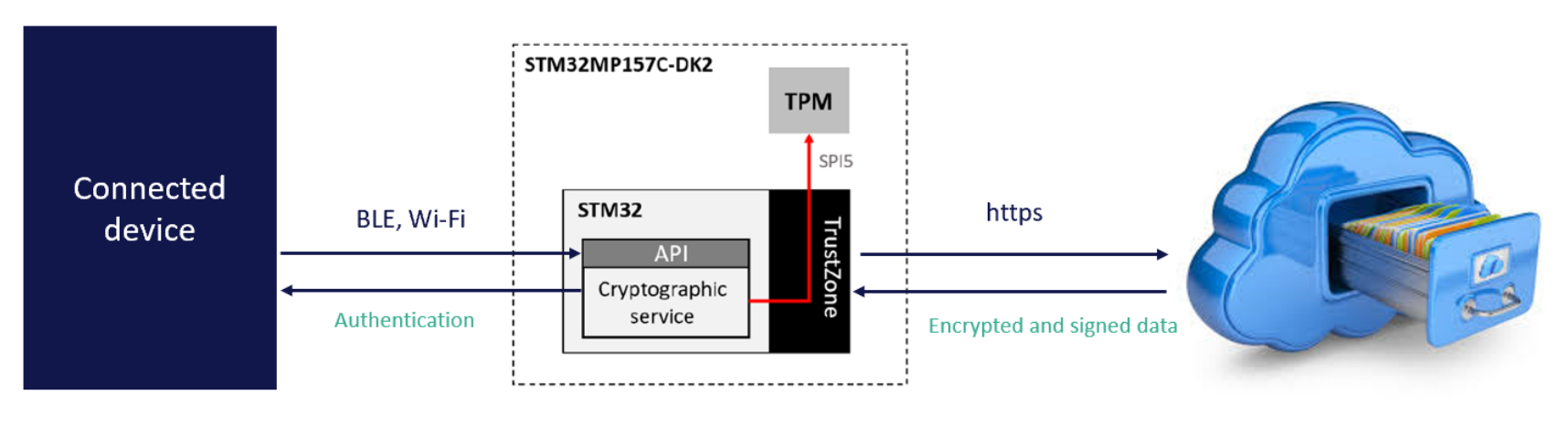
The idea was to take advantage of the Trustzone technology to have the non critical part of the Key Management System (KMS) running in the non-secure world while the sensitive cryptographic operations are executed in the TEE. To achieve this, a new backend for the cryptographic service was developed, taking advantage of the TEE supplicant instead of LibreSSL or a hardware HSM as it is the case with the existing backends.
The secure part of the application, running in OP-TEE is then proxying the cryptographic operation to the TPM. The TPM is used to store the master key and perform critical signature operations, thus allowing a maximal level of security at this stage. This way, even in case of physical access to the system, an attacker would have more difficulty retrieving the private keys.
The software stack was built using a reference distribution of Yocto Linux named Poky to build a minimal Linux system.
The cryptographic service is the main component of this project. It consists of a KMS developed by CYSEC in a micro-service architecture. The KMS is composed of a broker, a cryptographic service and a management tool, all written in Rust.
In a nutshell, the project included the achievement of the following tasks:
With this project, CYSEC has elaborated a distribution of its ARCA Trusted OS suitable for embedded devices.
Based on the results of SEGWAY, real-life applications have already been identified and deployed in multiple fields:
Learn more on how to securely run workloads with sensitive data on the cloud, on premise, and on the edge