The security guide for application containers published by NIST shows that the Operating System (OS) hosting the containers plays an important security role. ARCA Trusted OS, the container-specific OS from CYSEC includes implementations of many of the security countermeasures proposed by NIST. Adopting Arca Trusted OS lets companies benefit from a secure infrastructure even in an environment they do not own or control without compromising the agility gained by embracing container-based architecture.
The National Institute of Standards and Technology (NIST) has published a security guide on containerized applications referred to as SP 800-190. Its purpose is to explain the security concerns associated with container technologies and make practical recommendations for addressing those concerns when planning for, implementing, and maintaining containers. SP 800-190 sorts risks and countermeasures with respect to components present in a typical execution of containers: image, registry, orchestrator, container, host OS.
In the executive summary, NIST gives some general recommendations addressing each of these three entities: the organizations operating the containerized applications, the infrastructure hosting the containers, and the containerized applications.
CYSEC’s product called ARCA Trusted OS is implemented to cover the recommendations addressing the infrastructure hosting the containers. ARCA Trusted OS is a Linux-based micro-distribution specifically designed to run containers orchestrated by Kubernetes. This distribution provides a large range of security features aiming at limiting the possibility of system intrusion and at protecting data.
The table below summarizes how ARCA Trusted OS follows NIST guidelines for the host OS and for the hosting hardware.
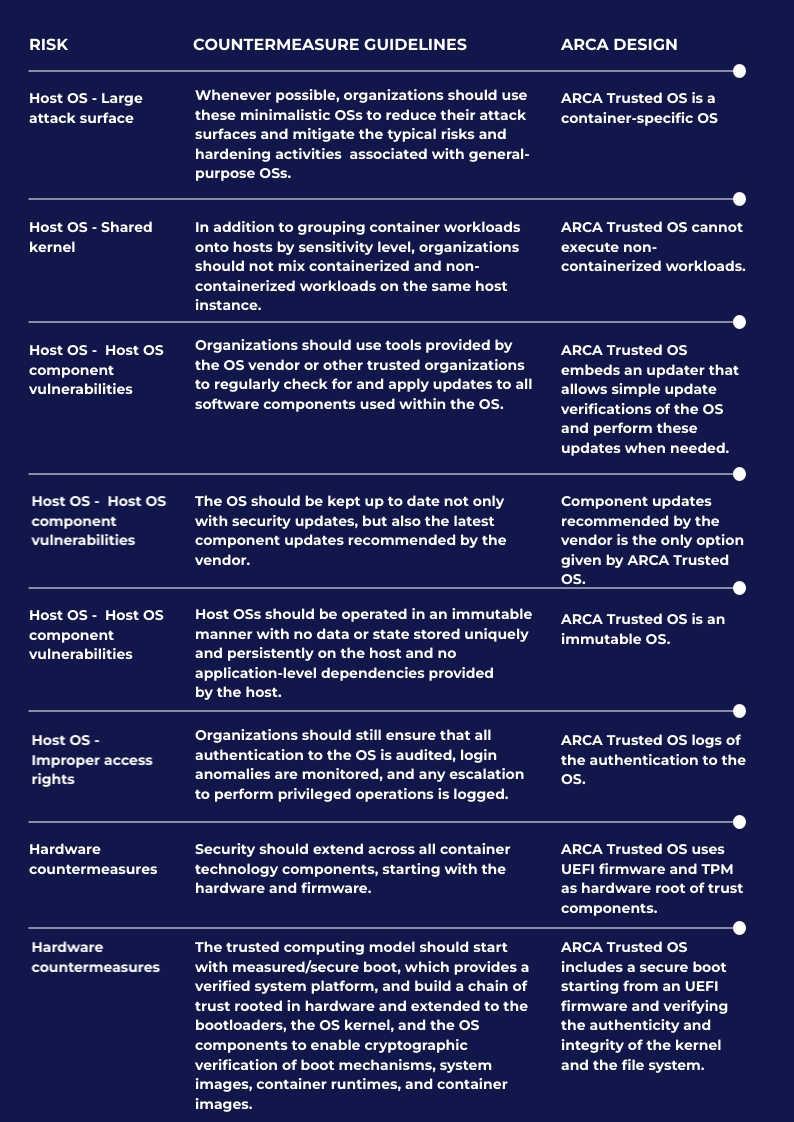
In addition to these recommendations specific to the host OS, ARCA Trusted OS follows some recommendations applying to images (such as countermeasures against the use of untrusted ARCA Trusted OS images), to registry (such as countermeasures against the insecure connection to registries), to orchestrator (such as data at-rest countermeasures allowing a transparent access this data by containers), and to container (such as the vulnerability monitoring of the container runtimes provided by ARCA Trusted OS).
Container based architecture such as Kubernetes offers companies to speed up time to market and scale up rapidly. It enables a “microservices” approach to building apps but as well to cut infrastructure costs significantly through automation by intelligently scheduling and tightly packing containers, taking into account the available resources.
While container-based architecture is an ideal solution to support business expansion, it presents many challenges that generally fall into security, networking, deployment, scaling, and vendor support categories. They’re at the forefront of setup and management and can make day-to-day tasks difficult if not addressed promptly and creates many vulnerabilities.
So, when enhancing companies’ mission critical processes and sensitive data within container-based architecture, Arca Trusted OS is the solution that simplifies the adoption of enhanced security layers in line with the NIST SP 800-190 recommendations, meanwhile keeping the agility the business is looking for in its development.