SECURE-BY-DESIGN EDGE COMPUTING SOLUTION
Edge computing is developing rapidly, driven by next-generation connected devices and fast communication links. Gartner predicts that by 2025, 75% of enterprise-generated data will be created and processed at the edge. As value shifts toward the edge, security gaps emerge in cloud-edge integration and edge devices become an entry point for attack.
Vulnerabilities exist at each building block of the edge ecosystem— the edge, the public cloud, and the endpoint. CYSEC ARCA is the first comprehensive trusted execution environment that secures data throughout the entire edge ecosystem.
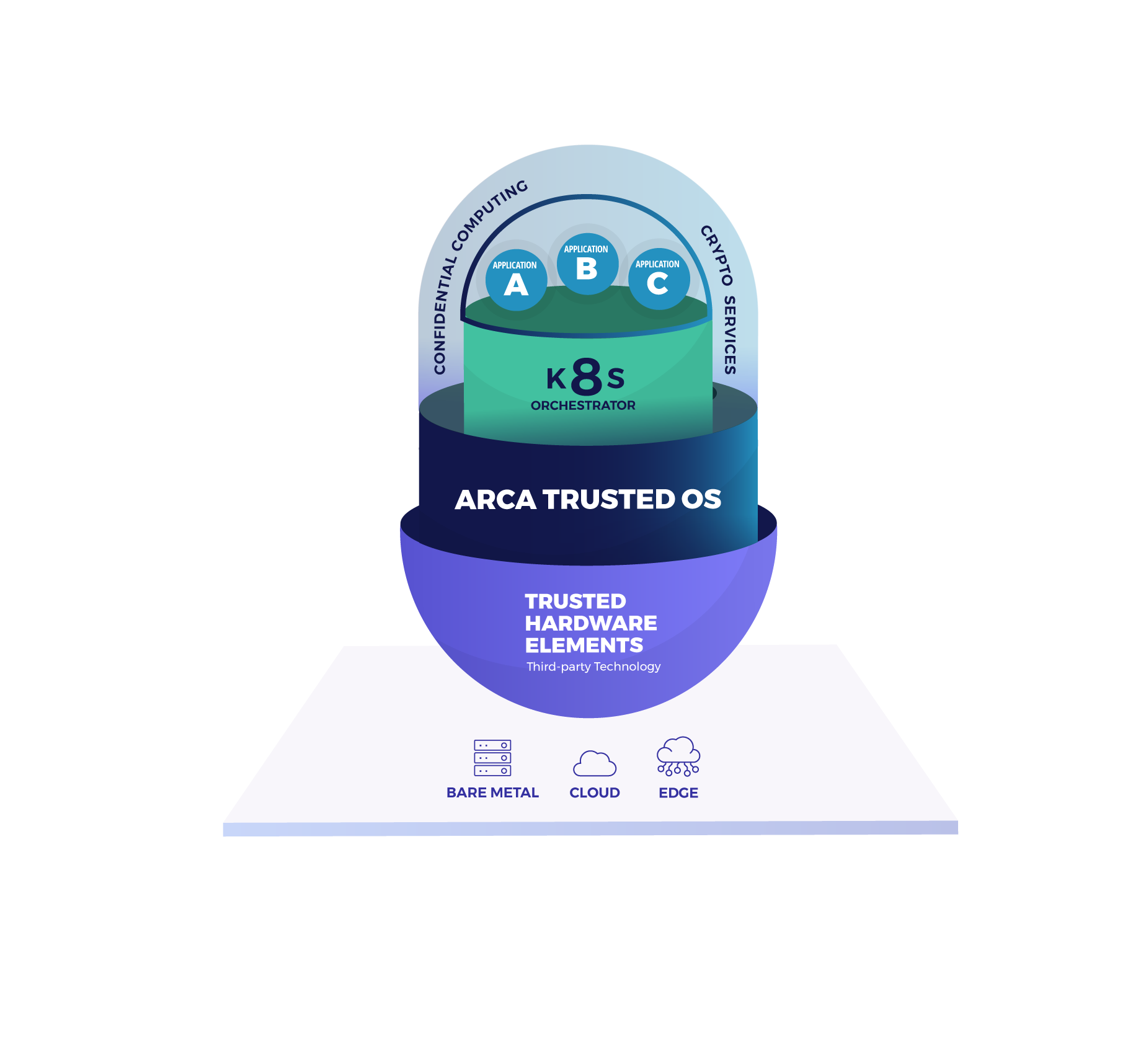
CYSEC ARCA gives you a full security solution, covering the edge and the back-end. It provides confidentiality and integrity of data collected at the edge, trust in application logic, and ensures attackers can’t use the edge to access your network.
ARCA is a trusted OS, designed to protect specific nodes up to end-to-end edge computing distributed architectures deployed from the core, the cloud and up to the edge. It benefits particularly companies looking to protect sensitive data and mission critical applications.

Edge devices rely on connectivity to transmit data collected by sensors. This data is high-value and transmitted to the cloud to deliver business intelligence and machine learning (ML). This connectivity opens a door to cyber criminals looking to take control of the device, move laterally in the network, eavesdrop on the high-value data, and disturb or interrupt critical services.
As a result, devices need to rely on a root of trust (RoT) for the secrets used in cryptographic operations behind data encryption or the authentication of other devices needed to communicate with the backend.
Further, edge devices need to be able to run critical software applications, perform firmware updates or data processing, in a confidential manner, making sure that an attacker cannot find a vulnerability to manipulate the code or data as it’s being processed.
Existing protection mechanisms compatible with embedded applications do not provide any protection for the data or code in use, nor are compatible with containerized software applications.